Pursue or approaching someone in a sneaky way is not remaining a surprise for everyone. Using technology stalking has become a phenomenon that has disturbed number of lives worldwide and it is on the rise with the advent of impressive pieces of technology in the shape of surveillance software. These types of tools that enable a user to do illicit and intrusive surveillance to keep an eye on someone’s personal life and even the activities they perform on their cell phones, gadgets, and computer machines. Stalkers are misusing the pieces of technology that has developed for parental control reasons or for employee monitoring purposes alongside the proper consent.
“Use of tech –tools by the stalkers is a very common practice these days”. The Associate Attorney General Perrelli said that at 15th Anniversary of the Violence against Women at a department of justice.
“No matter what we have to do in order to change the basics of these crimes and have to play a positive and effective role to make new plans to address stalking issues, he added that. “The law enforcement and our counterparts in the judiciary have to do serious stuff to eradicate the element of stalking and to rescue the victims, he further added that.
Technology that is cheap but capable of running to assist the stalkers to monitor and threaten the victims, he said further.
Stalkers are Quite a Tech-savvy
Stalkers over the years are using such a contemporary tech –tools in order to threaten the women and breaching their privacy by keeping a hidden eye on their digital activities and by tracking their location in real –time. But with the passage of time and with the help of awareness campaigns victims are learning the ways that how they can turntable over and beat the stalkers at their own game.
In What Ways Stalkers are Approaching Victims
According to the report of the department of justice, almost one-quarter of the 3.4 million stalking victims in the United States have reported cyber stalking through email tracking, instant messages monitoring, via GPS technology and plenty of other types of electronic monitoring were used to spy one out of 13 victims.
However, the tactics and circumstances are quite similar, but over the years the addition of technology even sometimes tricks with the law enforcement that is understaffed, under –rescued and under training. Stalkers can use social media apps such as Facebook, Yahoo, WhatsApp, Instagram and plenty of other platforms to approach their target via text messages, shared media files and emails as well. However, stalkers have many kinds such as cyber stalkers that want to stalk young and adult women for sexual needs and to manipulating them after having a relationship. Real –life stalkers that want to know each and every activity their victims does in real –lives in order to scare them .
Technology has not developed stalking but provides assistance
“The modern technology has not raised the evil of stalking, but it has made the easier for the stalkers to engage their target convincingly in a sneaky way, director of National Center for Victims of Crime’s Stalking Resources Center Michelle Garcia stated that. Most of the time the law enforcement officials could not able understand the technology that is been used against the victim as the victim are reporting.
How to prevent stalking without using technology?
If someone is using tech –tools that help the stalker to spy or in surveillance on the victim’s cell phone or computer device, then it would be obvious that digital stalking will leave behind the digital trail. Let’s suppose stalker is using the cyberspace and some kind of spyware tool to track the victim, it is possible that they can use lower tactics too. Stalkers are used of following victims using a vehicle in order to damage the property to scare the victim. You can fix tech –tools for the victims of home such as CCTV cameras, Voice recorder and many other things that can provide a solid clue to the law enforcement agencies.
Though the victims cannot monitor the videos in real-time, the fixed cameras in the house provide a piece of mind that they can provide an evidence of house breaching. On the other side of the victims has received Voice calls, text messages, emails, and other stuff from the stalker than the very first thing they should do to control their nerves and not to delete the received stuff via instant messengers, cell phone messages and others. This will really help out the law enforcement to catch the culprit red-handed. People who have been approached by the stalkers via internet such as social media platforms and through other tools should trust their instincts and they should inform the law enforcement agencies at the very first time they have been approached.
What measures TheOneSpy has taken to beat the stalkers?
The best cell phone and computer monitoring software believes in the world that is fair and free from all the online and real-life predators including cyber stalkers. TheOneSpy is basically a parental control and employee monitoring software that help out the parents to keep an eye on children digital and real-life activities and further empowers the employers to catch dishonest employees within the working hours if doing something fishy.
However, since the stalking is making headlines that stalkers are using the tech –tools for cyber stalking to breach the privacy online to threaten the victim. TheOneSpy has taken affirm actions to make sure that no stalker could be able to use the parenting software for illicit and intrusive surveillance such as stalking.
Though the cell phone parenting app has never been used for illegal purposes and we have set some ground rules before we are going to offer the license. We do verification process of the user and as well as the target such as children and employees. So, there is no chance that someone uses it for stalking. However, giving you a benefit of the doubt, if anyone has found using the parental control app for stalking, then we shall terminate the license effectively and immediately.
Further, we provide assistance to the target that they can sent us complain against the user and we will provide proof to the victim to sue the user in the court of law or to let law enforcement agencies to deal with the culprit or with alleged stalker.
TheOneSpy verification process in few steps:
TOS Par
ental control app for mobile phones and computers don’t let stalkers to use it for stalking having strong verification method as follows.
Step 1
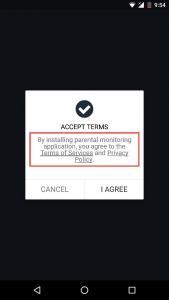
User has to accept our terms and conditions and privacy policy at the time of subscription and installation process.
Step 2
![]()
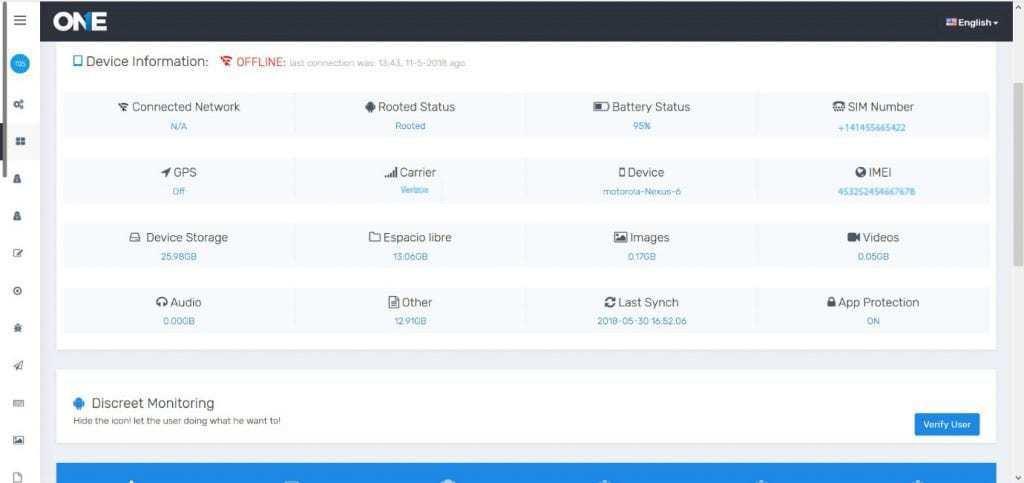
When user has ended up with installation of the mobile phone parenting app on the target device, then an icon will pop –up on the screen of the target device.
Step 3
TOS icon will remain visible at application manager and further on the Taskbar. Then user has to make a click on the symbol of an icon known as “padlock”.
Step 4
User will get a pop –up window that describe about parental control app is activated at back end. The icon will remain visible until and unless user want to make it sneaky. However, after every 4 to 5 hours padlock sign will appear on the target cell phone or gadget to inform the target person that someone is keeping a hidden eye on their activities to the fullest.
Step 5
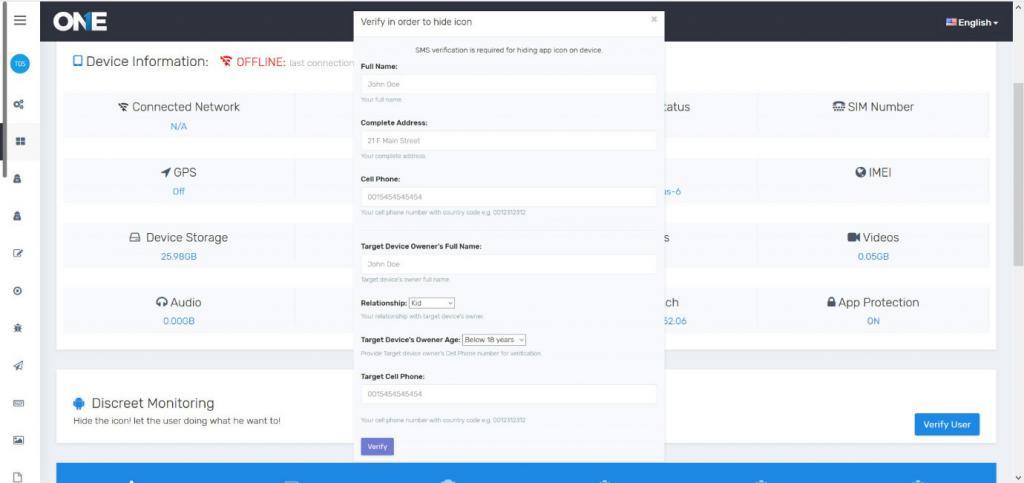
Buyer have to provide complete detail such as First Name, complete address, contact number, target device owner complete name, relationship such as kid or employee, target device user age and then have to verify his/her cell phone number as well. After the end of the verification process and all the information that buyer has provided us came true, then will keep a single of the verification process and send “Authorization form” to buyer email box.
Buyer violates the privacy policy: TOS provide complete assistance to victim
In-case if the victim has filed a complaint against the user then we will provide complete information of the user and let the victim and law enforcement agencies to deal with the stalker against the crime of intrusive and illicit surveillance.
Conclusion:
TheOneSpy is a parental control software that condemns the activity of stalking and doesn’t permit any user to use the parenting and employee monitoring software for illegal purposes. We make sure to protect the human rights in terms of privacy and we fully endorse the privacy is the fundamental right of every person worldwide no matter what color, creed and cast the person belongs to.